Bring Excellency With Our Expertise
Is your company’s sensitive data
at risk?
WE CAN HELP YOU!
WE CAN HELP YOU!
















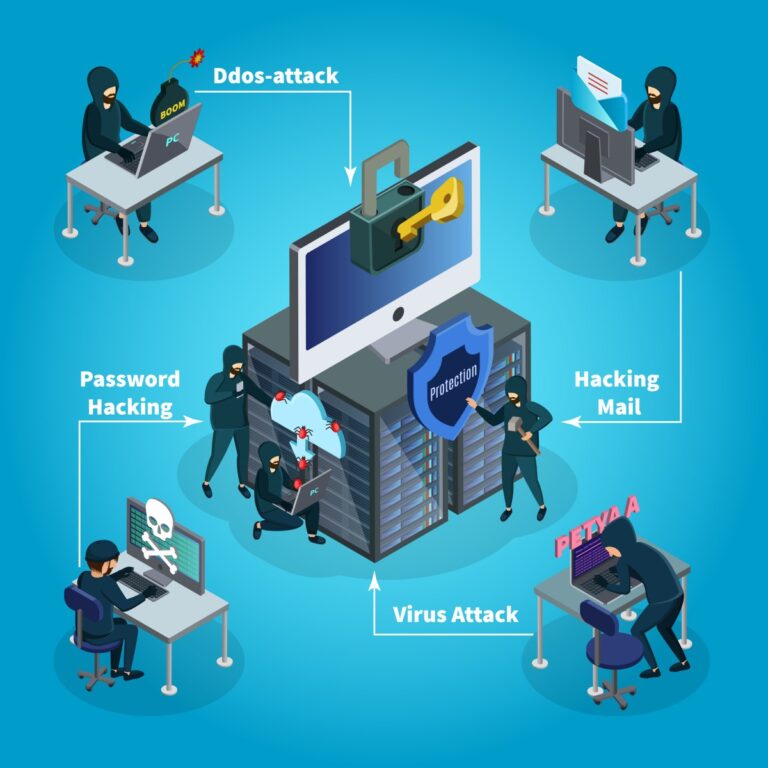
Our specialist quality team will make sure your security.

a. Virus/Ransomware
b. Infected portable devices
c. Social networking or malicious web browsing
d. Chats
e. Printout of classified information
f. Emails
g. File uploads to untrusted medium
h. Email attachment
i. Unintentional or negligent data exposure

a. Access control list
b. Single sign on
c. Desktop standardization
a. System monitoring
b. Scanning data at rest
c. Personal information protection
d. Generating informative alerts
e. Blocking the internal threats
f. Security policy
